Ever wonder what network traffic a process is generating in Windows? Well we had a problem with a service at work this week and I had just that need and found a nifty way to find out…read on for details!
Of course as this deals with Windows, the tool I used was created by the one and only Mark Russinovich who it would appear single handely wrote every handy little tool for Windows. The tool is Process Monitor and does much more than my particular need but nailed what I needed to find out: what network traffic was a process generating?
To filter out out all the noise I identified the process ID from the Task Manager and then created two filters:
- Filter on the process’s PID
- Filter on operations that have TCP in the name
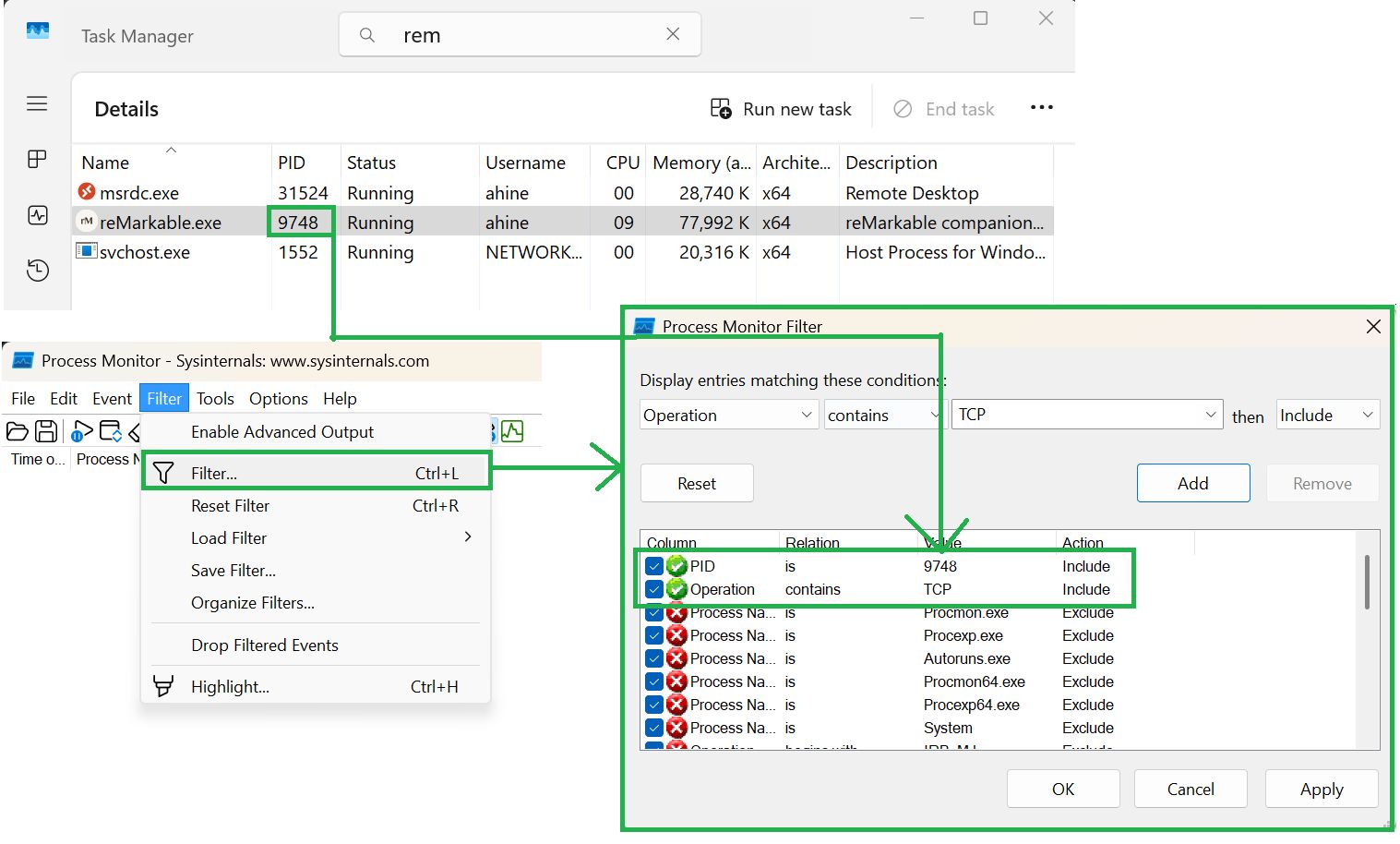
And now we can see what traffic the process is generating:
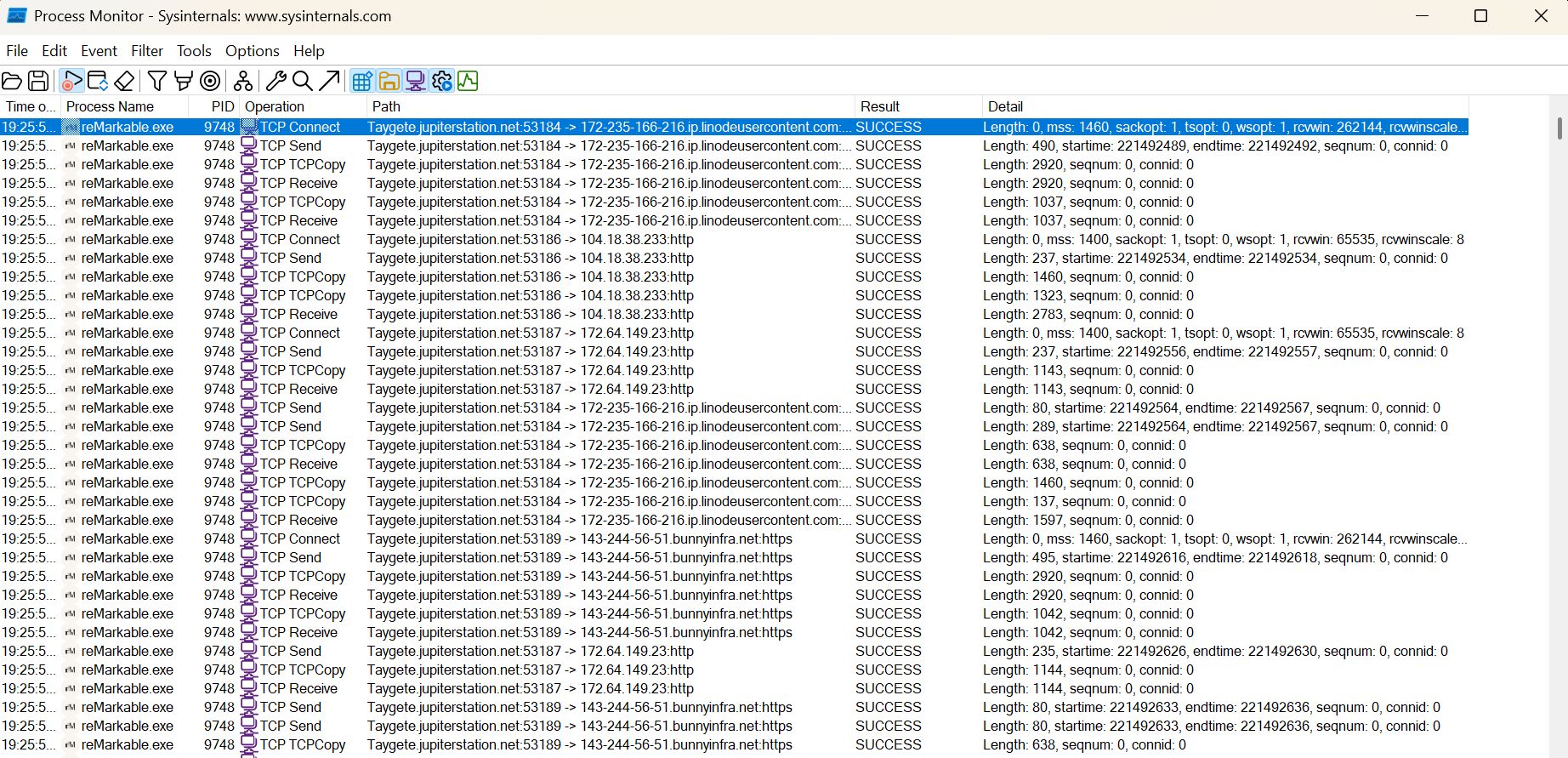
In the service outage I used this in conjunction with Wireshark adding a filter for all the destination IPs and we quickly saw that some traffic was receiving a TCP RST from one of the servers after doing the TLS tango, a clear sign that a layer 7 firewall did not like something and was tearing down the communication channel, which was what we suspected, but until we could prove it no one believed us…
Links, References and things that helped with this
Thanks for reading and feel free to give feedback or comments via email (andrew@jupiterstation.net).